
آنچه در این صفحه می خوانید:
- معرفی شبکه (Computer network)
- سرویس ها و ابزار های شبکه
- انواع شبکه
- دامنه سازمانی شبکه
- گواهینامه ها و آزمون های شبکه
معرفی شبکه (Computer network)
شبکه رایانه ای (Computer network) یک شبکه ارتباطی دیجیتال است که به گره ها (سیستم ها) امکان به اشتراک گذاری منابع را می دهد. در شبکه های رایانه ای، دستگاه های محاسباتی با استفاده از اتصالات (پیوند داده) بین گره ها، داده ها را با یکدیگر تبادل می کنند. این پیوندهای داده از طریق رسانه های کابل مانند کابل های زوج به هم تابیده یا فیبر نوری و یا رسانه های بی سیم مانند Wi-Fi برقرار می شوند. به دستگاه های رایانه ای شبکه که مبدا، مسیریابی و خاتمه داده ها هستند، گره های شبکه گفته می شود. گره ها به طور کلی توسط آدرس های شبکه مشخص می شوند و می توانند میزبان هایی مانند رایانه های شخصی، تلفن ها و سرورها و همچنین سخت افزارهای شبکه مانند روترها و سوئیچ ها را در بر گیرند. می توان گفت هنگامی که یک دستگاه قادر به تبادل اطلاعات با دستگاه دیگر باشد، چه ارتباط مستقیمی با یکدیگر داشته باشد یا نه، می توان گفت دو دستگاه از این دست به هم شبکه می شوند. در بیشتر موارد، پروتکل های ارتباطی خاص برنامه کاربردی بیش از سایر پروتکل های ارتباطی عمومی تر لایه بندی می شوند. این مجموعه قدرتمند فناوری اطلاعات نیاز به مدیریت ماهر شبکه دارد تا بتواند همه این موارد را با اطمینان اجرا کند.
شبکه های رایانه ای تعداد بسیار زیادی از برنامه ها و خدمات مانند دسترسی به شبکه جهانی وب، فیلم دیجیتال، صوتی دیجیتال، استفاده مشترک از سرورهای برنامه و ذخیره سازی، چاپگرها و دستگاه های فکس و استفاده از برنامه های ایمیل و پیام فوری و همچنین بسیاری دیگر. شبکه های رایانه ای در رسانه انتقال مورد استفاده برای حمل سیگنال های خود، پروتکل های ارتباطی برای سازماندهی ترافیک شبکه، اندازه شبکه، توپولوژی، مکانیسم کنترل ترافیک و اهداف سازمانی متفاوت هستند. شناخته شده ترین شبکه رایانه ای اینترنت است.
معرفی مفهوم شبکه کردن
شبکه های رایانه ای اساس ارتباطات در فناوری اطلاعات هستند. آنها به روش های گوناگونی مورد استفاده قرار می گیرند و می توانند انواع مختلفی از شبکه را شامل شوند. شبکه رایانه ای مجموعه رایانه هایی است که به هم وصل شده اند تا بتوانند اطلاعات را به اشتراک بگذارند. اولین نمونه های شبکه های رایانه ای از دهه 1960 میلادی است، اما از آن زمان تاکنون در نیم قرن راه طولانی داشته اند.
شبکه رایانه ای مجموعه رایانه هایی است که به منظور به اشتراک گذاری منابع به هم متصل شده اند. متداول ترین منبع مشترک امروز ارتباط با اینترنت است. سایر منابع مشترک می توانند شامل چاپگر یا سرور پرونده باشند. خود اینترنت را می توان یک شبکه رایانه ای دانست.
شبکه رایانه ای مجموعه ای از رایانه های متصل به هم است. رایانه های موجود در شبکه گره نامیده می شوند. اتصال بین رایانه ها از طریق کابل کشی، معمولاً کابل اترنت یا کابل فیبر نوری قابل انجام است. اتصالات همچنین می توانند بی سیم باشند. شما اصطلاح wi-fi را برای توصیف اطلاعات ارسال شده از طریق امواج رادیویی می شنوید.
کامپیوترهای متصل می توانند منابعی مانند دسترسی به اینترنت، چاپگرها، فایل سرورها و سایر موارد را به اشتراک بگذارند. شبکه یک اتصال چند منظوره است که به یک رایانه واحد اجازه می دهد بیش از آنچه ممکن است بدون هیچ ارتباطی انجام دهد.
واژه های کلیدی شبکه
سیستم باز (Open system): یک سیستم باز به شبکه وصل شده و برای ارتباط آماده شده است.
سیستم بسته (Closed system): یک سیستم بسته به شبکه وصل نمی شود و بنابراین نمی توان با آن ارتباط برقرار کرد.
آدرس IP (پروتکل اینترنت): آدرس شبکه سیستم در سراسر شبکه، که به عنوان آدرس منطقی نیز شناخته می شود).
آدرس MAC: آدرس MAC یا آدرس فیزیکی منحصر به فرد هر میزبان را مشخص می کند. با کارت رابط شبکه (NIC) همراه است.
پورت (Port): پورت كانالي است كه از طريق آن داده ها ارسال و دريافت مي شوند.
گره ها (Nodes): گره ها اصطلاحی است که برای اشاره به دستگاه های محاسباتی مانند رایانه هایی که بسته های شبکه را از طریق شبکه ارسال و دریافت می کنند، استفاده می شود.
بسته های شبکه (Network packets): داده هایی که از طریق گره های یک شبکه به و از آن ارسال می شوند.
روترها (Routers): روترها قطعات سخت افزاری هستند که بسته های روتر را مدیریت می کنند. آنها تعیین می کنند که کدام گره اطلاعات از کجا ارسال شده و از کجا می تواند آن را ارسال کند. روتر دارای پروتکل مسیریابی است که نحوه برقراری ارتباط با سایر روترها را تعریف می کند.
ترجمه آدرس شبکه (NAT): روشی که روترها برای ارائه خدمات اینترنتی به دستگاههای بیشتری با استفاده از IP های عمومی كمتر استفاده می كنند. روتر دارای یک آدرس IP عمومی است اما به دستگاههای متصل به آن IP های خصوصی اختصاص داده شده است که دیگران خارج از شبکه نمی توانند آن را ببینند.
پروتکل پیکربندی هاست پویا (DHCP): آدرس IP پویا را به هاست اختصاص می دهد و توسط ارائه دهنده خدمات اینترنت نگهداری می شود.
ارائه دهنده سرویس اینترنت (ISP): شرکت هایی که ارتباط اینترنتی خود را برای همه و افراد و همچنین مشاغل و سازمان های دیگر در اختیار همه قرار می دهند.
لایه های شبکه
مدل ارتباطات Open Systems (مدل OSI) یک مدل مفهومی است که عملکردهای ارتباطی یک سیستم ارتباطی یا محاسباتی را بدون در نظر گرفتن ساختار و فن آوری داخلی اساسی آن، توصیف و استاندارد سازی می کند. هدف آن قابلیت همکاری سیستم های ارتباطی متنوع با پروتکل های ارتباطی استاندارد است. این مدل یک سیستم ارتباطی را به لایه های انتزاع تقسیم می کند. نسخه اصلی مدل دارای هفت لایه بود. یک لایه به لایه بالای آن خدمت کرده و توسط لایه زیر آن سرو می شود. به عنوان مثال، لایه ای که ارتباطات عاری از خطا را در سراسر شبکه فراهم می کند، مسیر مورد نیاز برنامه های بالای آن را فراهم می کند، در حالی که لایه زیرین بعدی را برای ارسال و دریافت بسته هایی تشکیل می دهد که محتوای آن مسیر را تشکیل می دهند. دو نمونه در یک لایه همانطور که توسط یک اتصال افقی در آن لایه متصل می شوند، تجسم می شوند. این مدل محصولی از پروژه Open Systems Interconnection در سازمان بین المللی استاندارد سازی (ISO) است.
هفت لایه شبکه عبارتند از:
- لایه فیزیکی ()Physical layer
- لایه پیوند داده (Data link layer)
- لایه شبکه (Network layer)
- لایه انتقال (Transport layer)
- لایه نشست (Session layer)
- لایه ارائه (Presentation layer)
- لایه اپلیکیشن (Application layer)
مفاهیم TCP و UDP
پروتکل های پیاده سازی شده توسط TCP / IP Services و استفاده شده توسط CICS TCP / IP در زیر نشان داده شده است:
- پروتکل کنترل انتقال (TCP)
از نظر مدل OSI، TCP یک پروتکل لایه حمل و نقل است. این یک اتصال مدار مجازی قابل اعتماد بین برنامه ها را فراهم می کند. یعنی قبل از شروع انتقال داده، اتصال برقرار می شود. داده ها بدون خطا یا کپی ارسال می شوند. هیچ محدودیتی بر داده ها تحمیل نشده است. TCP با داده ها به عنوان جریانی از بایت رفتار می کند.
- پروتکل داده کاربر (UDP)
UDP همچنین یک پروتکل لایه حمل و نقل است و جایگزینی برای TCP است. این یک اتصال داده غیر قابل اعتماد بین برنامه ها را فراهم می کند. داده ها از طریق لینک به لینک انتقال داده می شوند. هیچ ارتباط انتهایی به پایان وجود ندارد. این سرویس هیچ تضمینی ارائه نمی دهد. داده ها را می توان از دست داد یا کپی کرد و داده ها می توانند از حالت خارج شوند.
سرویس ها و ابزار های شبکه
شبکه سازی TCP / IP، مدیریت شبکه و مبانی پیکربندی سیستم را پوشش می دهد. لینوکس می تواند از چندین دستگاه شبکه پشتیبانی کند.
ویندوز سرور گروهی از سیستم عامل است که توسط مایکروسافت طراحی شده است و از مدیریت سطح سازمانی، ذخیره داده ها، پایگاه های داده، برنامه ها و ارتباطات پشتیبانی می کند. نسخه های قبلی ویندوز سرور بر ثبات، امنیت، شبکه سازی و پیشرفت های مختلف سیستم فایل متمرکز شده است. سایر پیشرفت ها همچنین شامل پیشرفت در فناوری های استقرار و همچنین افزایش پشتیبانی از سخت افزار است. مایکروسافت همچنین SKU های ویژه ویندوز سرور ایجاد کرده است که بر بازارهای خانگی و تجارت کوچک متمرکز شده اند.
اکتیو دایرکتوری (Active Directory)
یک سرویس دایرکتوری است که توسط مایکروسافت برای شبکه های دامنه ویندوز ایجاد شده است. این برنامه در اکثر سیستم عامل های ویندوز سرور به عنوان مجموعه ای از فرآیندها و سرویس ها گنجانده شده است. در ابتدا، Active Directory فقط مسئولیت مدیریت متمرکز دامنه را بر عهده داشت. سروری که سرویس دامنه Active Directory را اجرا می کند کنترلر دامنه نامیده می شود. این برنامه به کاربران و رایانه های موجود در یک شبکه از نوع دامنه ویندوز، تعیین خط مشی های امنیتی برای همه رایانه ها و نصب یا به روز رسانی نرم افزار تأیید می کند.
یک شبکه را فراهم می کند که می تواند به طور ایمن و قابل اطمینان انواع ترافیک را در کل شبکه، تقریبا در هر رسانه ای اداره کند، در حالیکه ارائه خدمات منسجم برای همه کاربران را فراهم می کند. سیسکو می تواند یک شبکه end-to-end متشکل از سیستم هایی است که به طور خاص برای پاسخگویی به نیازهای منحصر به فرد هر مکان در شبکه طراحی شده اند و به زیرساخت مشترک و یک سیستم عامل مشترک متصل اند و از یک مکان مرکزی به عنوان یک واحد انسجام قابل مدیریت هستند. از آنجایی که Cisco شبکه را به عنوان یک کل در نظر می گیرد، محصولات و فن آوری ها و راه حل هایی را ارائه می دهد که مزایای تجاری را در کل شبکه ایجاد می کند. سیسکو مدیریت شبکه و ابزارهای لازم برای مدیریت شبکه را به طور کامل اداره می کند. علاوه بر این، سیسکو ارتباط بین تمام عناصر شبکه را درک می کند.
انواع قابلیت های شبکه ای مانند اتصال بین منابع Azure، اتصال به اینترنت، اتصال محلی، تعادل بار و جهت ترافیک، امنیت شبکه، مسیریابی، نظارت و مدیریت منابع شبکه Azure و ابزارهای نصب و راه اندازی منابع شبکه را فراهم می کند که می تواند با هم یا جداگانه مورد استفاده قرار گیرد.
توانایی راه اندازی شبکه های پیشرفته با ماشین های مجازی را دارد. با استفاده از تکنیک مناسب، می توان به ماشین های مجازی از شبکه محلی دسترسی داشت و مسیر بین چندین ماشین مجازی را پیکربندی کرد. هر زمان که یک ماشین مجازی را از wizard پیکربندی کنید، به طور خودکار با یک آداپتور شبکه مجازی پیکربندی شده است. در VMware Workstation، شما می توانید تا سه آداپتور شبکه مجازی را در هر دستگاه مجازی داشته باشید. در VMware، سوئیچ ها برای برقراری ارتباط بین شبکه مجازی و شبکه فیزیکی استفاده می شود.
شرکت کامپتیا (CompTIA)
یک سازمان مستقل اختصاصی برای ایجاد جامعه و ارتقای برتر در صنعت فناوری اطلاعات رایانه های جهانی محسوب می شود. CompTIA امتحانات صدور گواهینامه دز زمینه های مختلف از جمله امنیت، شبکه و لینوکس ارائه می دهد. در زمینه درک عمیق از زیرساخت های شبکه و توانایی نصب، پیکربندی، مدیریت و نگهداری شبکه ها آزمون گواهی نامه ی CompTIA Network Plus را برگزار می کند که برای مدیران شبکه، تحلیلگران امنیتی و مهندسین سیستم کاربرد دارد. در زمینه ی امنیت، CompTIA Security Plus را ارائه می دهد که دانشی از زیرساخت های شبکه، امنیت سیستم، حسابرسی، رمزنگاری و غیره را فراهم می کند که برای تحلیلگران امنیتی و مهندسین سیستم مفید است.
به کامپیوتر هایی که به یکدیگر متصل اند و یک اکوسیستم واحد یا یک شبکه را تشکیل دادند می گویند که این امکان را برای سرورها، حافظه های ذخیره سازی و برنامه های کاربردی فراهم می کند تا از طریق اینترنت، به کامپیوترها و تمامی دستگاه های متصل به اینترنت سازمان ها دسترسی داشته باشد.
وب سرویس آمازون (AWS) یک شرکت تابعه آمازون است که سیستم های محاسبات ابری را در صورت تقاضا برای افراد، شرکت ها و دولت ها در صورت پرداخت مبلغ ارائه می دهد. درمجموع، این سرویس های وب رایانش ابری مجموعه ای از زیرساخت های فنی انتزاعی اولیه و بلوک های ساختمان و محاسبات توزیع شده را ارائه می دهند. یکی از این خدمات Amazon Elastic Compute Cloud است که به کاربران این امکان را می دهد تا یک خوشه مجازی رایانه که در تمام مدت از طریق اینترنت در دسترس است، در اختیار داشته باشند. نسخه رایانه های مجازی AWS بیشتر ویژگی های رایانه واقعی را شامل می شود، شامل واحدهای پردازش مرکزی سخت افزاری (CPU) و واحدهای پردازش گرافیکی (GPU) برای پردازش، حافظه محلی / RAM، حافظه دیسک سخت / SSD می باشد. انتخاب سیستم عامل ها؛ شبکه و نرم افزارهای از قبل بارگذاری شده مانند سرورهای وب، بانک های اطلاعاتی، مدیریت ارتباط با مشتری (CRM) و غیره.
یک منبع نرم افزار اوپن سورس برای مدیریت پیکربندی و ابزار استقرار برنامه است. این سیستم بر روی بسیاری از سیستم های مانند یونیکس اجرا می شود و می تواند هم سیستم های یونیکس مانند و هم مایکروسافت ویندوز را پیکربندی کند. Ansible یک موتور IT ساده است که استقرار نرم افزار، intra service orchestration، cloud provisioning و سایر ابزارهای IT خودکار می سازد. استقرار Ansible آسان است زیرا از هیچ عامل یا زیرساخت امنیتی سفارشی استفاده نمی کند.
MikroTik تولید کننده تجهیزات شبکه است. این شرکت روترهای شبکه کابلی و بی سیم، سوئیچ شبکه، اکسس پوینت و همچنین سیستم عامل ها و نرم افزارهای کمکی را توسعه داده و می فروشد. تجربه میکروتیک در استفاده از سخت افزار PC استاندارد صنعتی و سیستم های مسیریابی کامل باعث شد در سال 1997 سیستم نرم افزاری RouterOS را ایجاد کند که ثبات، کنترل و انعطاف پذیری گسترده ای را برای انواع واسط های داده و مسیریابی فراهم می کند.
Microsoft Azure که قبلا Windows Azure نامیده می شد یک سرویس محاسباتی ابری است که توسط مایکروسافت از طریق مراکز داده مدیریت شده برای ساخت، تست، توسعه و مدیریت برنامه ها و سرویس ها ایجاد شده است. مایکروسافت، Azure را به عنوان یک سیستم جهانی مبتنی بر ابر ساخته است که در ادغام سرویس های مختلف مانند پلتفرم به عنوان سرویس (PaaS)، زیرساخت به عنوان یک سرویس (IaaS) و نرم افزار به عنوان سرویس (SaaS) پیشرفت چشم گیری داشته است. این سرویس ها بسیار انعطاف پذیر هستند و همچنین از بسیاری از زبان های برنامه نویسی مختلف، ابزارها و فریمورک ها، از جمله نرم افزار و سیستم های خاص و شخص ثالث پشتیبانی می کند.
به عبارت ساده، VMware نرم افزار مجازی سازی را توسعه می دهد. نرم افزار مجازی سازی یک لایه انتزاعی را بر روی سخت افزار رایانه ایجاد می کند که اجازه می دهد عناصر سخت افزاری یک رایانه مانند پردازنده، حافظه، فضای ذخیره سازی و موارد دیگر، به چندین رایانه مجازی تقسیم شوند که معمولاً به آنها ماشین های مجازی (VMs) گفته می شود. هر دستگاه مجازی سیستم عامل خود را اجرا می کند و مانند یک کامپیوتر مستقل رفتار می کند، حتی اگر روی بخشی از سخت افزار رایانه ای اساسی کار کند.
Nginx یک وب سرور است که می تواند به عنوان پروکسی معکوس، متعادل نمودن بار ترافیکی، پروکسی ایمیل و حافظه نهان HTTP نیز مورد استفاده قرار گیرد و به عنوان یک وب سرور جهت حداکثر عملکرد و ثبات طراحی شده است. Nginx نرم افزاری رایگان و اوپن سورس است که تحت شرایطی مانند مجوز BSD مانند منتشر شده است. بخش بزرگی از وب سرورها از NGINX، غالباً به عنوان متعادل کننده بار ترافیکی استفاده می کنند.
Wireshark یک آنالایزر پروتکل شبکه رایگان و اوپن سورس است. برای عیب یابی شبکه، تجزیه و تحلیل، توسعه پروتکل نرم افزار و ارتباطات و آموزش استفاده می شود. وایرشارک کراس پلتفرم است، با استفاده از ابزار ابزارک Qt در نسخه های فعلی برای پیاده سازی رابط کاربری خود و استفاده از pcap برای گرفتن بسته ها به کار گرفته می شود. این برنامه در لینوکس، macOS ،BSD ،Solaris برخی از سیستم عامل های مشابه یونیکس و Microsoft Windows اجرا می شود. همچنین نسخه مبتنی بر ترمینال (غیر GUI) با نام TShark وجود دارد. Wireshark و سایر برنامه های توزیع شده با آن مانند TShark، نرم افزاری رایگان هستند که تحت شرایط مجوز عمومی GNU منتشر می شوند.
وایرشارک مهمترین و گسترده ترین آنالایزر پروتکل شبکه در جهان است. این امکان را برای شما فراهم می کند تا ببینید که چه اتفاقی در شبکه شما در سطح میکروسکوپی رخ می دهد و دارای استاندارد de facto (و اغلب de jure) در بسیاری از شرکت های تجاری و غیرانتفاعی، آژانس های دولتی و مؤسسات آموزشی است. توسعه Wireshark به لطف کمک های داوطلبانه کارشناسان شبکه در سراسر جهان پیشرفت می کند و ادامه پروژه ای است که توسط جرالد کامبز در سال 1998 آغاز شد.
انواع شبکه
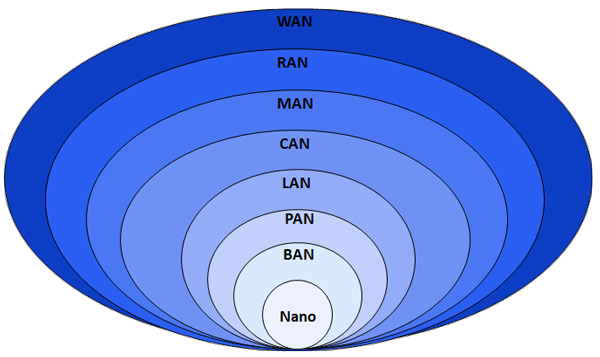
یک شبکه را می توان از نظر ظرفیت بدنی یا هدف سازمانی آن مشخص کرد. استفاده از شبکه، از جمله مجوز کاربر و حقوق دسترسی، بر این اساس متفاوت است.
شبکه نانو (Nanoscale)
یک شبکه ارتباطی نانو دارای مؤلفه های کلیدی است که در مقیاس نانو از جمله حامل پیام و اصول فیزیکی اهرم های مختلف که با مکانیسم های ارتباطی کلان متفاوت است، اجرا شده است. ارتباطات نانومقیاس ارتباطات را با حسگرها و محرک های بسیار کوچک مانند آن هایی که در سیستم های بیولوژیکی یافت می شوند گسترش می دهد و همچنین تمایل به فعالیت در محیط هایی دارد که برای ارتباطات کلاسیک خیلی سخت باشد.
شبکه محلی شخصی (Personal area)
شبکه منطقه شخصی (PAN) یک شبکه رایانه ای است که برای ارتباط بین رایانه ها و دستگاه های مختلف فن آوری اطلاعات نزدیک به یک نفر مورد استفاده قرار می گیرد. برخی از نمونه دستگاه هایی که در PAN استفاده می شوند عبارتند از: رایانه های شخصی، چاپگرها، دستگاه های فکس، تلفن، PDA ها، اسکنرها و حتی کنسول های بازی ویدیویی. یک PAN ممکن است دستگاه های سیمی و بی سیم باشد. دسترسی به یک پانل به طور معمول تا 10 متر گسترش می یابد. یک PAN سیمی معمولاً با اتصالات USB و FireWire ساخته می شود در حالی که فناوری هایی مانند بلوتوث و ارتباطات مادون قرمز معمولاً یک PAN بی سیم تشکیل می دهند.
شبکه محلی (Local area)
شبکه محلی (LAN) شبکه ای است که رایانه ها و دستگاه ها را در یک منطقه جغرافیایی محدود مانند خانه، مدرسه، ساختمان اداری یا گروهی از ساختمان ها که از نزدیک موقعیت دارند متصل می کند. هر رایانه یا دستگاهی در شبکه یک گره است. LAN های سیمی به احتمال زیاد براساس فناوری اترنت ساخته شده اند. همچنین استانداردهای جدیدتری مانند ITU-T G.hn راهی برای ایجاد یک شبکه سیمی با استفاده از سیم کشی موجود مانند کابل های کواکسیال، خطوط تلفن و خطوط برق فراهم می کند.
ویژگی های تعیین کننده یک شبکه، برخلاف شبکه گسترده (WAN)، شامل نرخ انتقال داده بالاتر، محدوده محدود جغرافیایی و عدم اتکا به خطوط اجاره ای برای تأمین اتصال است. اترنت فعلی یا سایر فن آوری های IEEE 802.3 LAN با سرعت انتقال داده تا 100 گیگابیت بر ثانیه، استاندارد شده توسط IEEE در سال 2010 عمل می کنند. در حال حاضر، 400 گیگابیت در ثانیه اترنت در حال توسعه است. با استفاده از روتر می توان LAN را به WAN وصل کرد.
شبکه محلی خانگی (Home area)
شبکه محلی (HAN) یک شبکه مسکونی (LAN) مسکونی است که برای برقراری ارتباط بین دستگاه های دیجیتالی که معمولاً در خانه مستقر هستند، معمولاً تعداد کمی از رایانه ها و لوازم جانبی شخصی مانند چاپگرها و دستگاه های محاسبات تلفن همراه مورد استفاده قرار می گیرد. یک عملکرد مهم به اشتراک گذاری دسترسی به اینترنت است که اغلب یک سرویس باند پهن از طریق تلویزیون کابلی یا ارائه دهنده خط مشترک دیجیتال (DSL) است.
شبکه ذخیره سازی (Storage area)
شبکه منطقه ذخیره سازی (SAN) یک شبکه اختصاصی است که دسترسی به ذخیره سازی داده های تلفیقی و سطح بلوک را فراهم می کند. SAN ها در درجه اول برای ساختن وسایل ذخیره سازی از قبیل آرایه های دیسک، کتابخانه های نوار و جعبه های نوری قابل دسترسی برای سرورها مورد استفاده قرار می گیرند تا دستگاه ها مانند دستگاه های محلی به سیستم عامل متصل شوند. سان به طور معمول دارای شبکه ذخیره سازی مخصوص به خود است که بطور کلی توسط سایر دستگاه ها از طریق شبکه محلی قابل دسترسی نیست. هزینه و پیچیدگی SAN در اوایل دهه 2000 کاهش یافت و به سطحی رسید که امکان پذیرش گسترده تری در محیط های تجاری و کوچک و متوسط را فراهم کرد.
شبکه فضای باز (Campus area)
یک شبکه منطقه فضای باز (CAN) از اتصال شبکه های LAN در یک منطقه جغرافیایی محدود تشکیل شده است. تجهیزات شبکه (سوئیچ، روتر) و رسانه انتقال (فیبر نوری، کارخانه مس، کابل کشی Cat5 و غیره) تقریباً به طور کامل متعلق به مستاجر / مالک دانشگاه (یک شرکت، دانشگاه، دولت و غیره) است. به عنوان مثال، یک شبکه فضای باز دانشگاه ها احتمالاً انواع مختلف ساختمان دانشگاه را بهم متصل می کند تا کالج ها یا ادارات دانشگاهی، کتابخانه و سالن های اقامت دانشجویی را به هم وصل کند.
شبکه Backbone
یک شبکه Backbone بخشی از زیرساخت های شبکه رایانه ای است که مسیری برای تبادل اطلاعات بین شبکه های مختلف LAN یا زیر شبکه فراهم می کند. Backbone می تواند شبکه های متنوعی را در همان ساختمان، در ساختمان های مختلف یا بیش از یک منطقه وسیع به هم وصل کند. به عنوان مثال، یک شرکت بزرگ ممکن است یک شبکه Backboneرا برای اتصال بخش هایی که در سراسر جهان واقع شده اند، پیاده سازی کند. تجهیزاتی که شبکه های اداری را به هم وصل می کنند Backbone شبکه است. هنگام طراحی Backbone شبکه، عملکرد شبکه و احتقان شبکه فاکتورهای مهمی است که باید در نظر گرفته شود. به طور معمول، ظرفیت شبکه Backbone از شبکه های انفرادی متصل به آن بیشتر است. نمونه دیگر شبکه بک گراند Backbone اینترنت است که یک سیستم عظیم جهانی کابل فیبر نوری و شبکه نوری است که بخش عمده ای از داده ها را بین شبکه های گسترده (WAN)، مترو، منطقه ای، ملی و شبکه های فرامرزی حمل می کند.
شبکه منطقه شهری (Metropolitan area)
یک شبکه منطقه متروپولیتن (MAN) یک شبکه رایانه ای بزرگ است که معمولاً در یک شهر یا یک دانشگاه بزرگ قرار دارد.
شبکه گسترده (Wide area)
شبکه گسترده (WAN) یک شبکه رایانه ای است که منطقه جغرافیایی بزرگی مانند شهر، کشور یا حتی مسافت های بین قاره ای را در بر می گیرد. WAN از یک کانال ارتباطی استفاده می کند که انواع بسیاری از رسانه ها مانند خطوط تلفن، کابل ها و امواج هوایی را در خود جای داده است. WAN اغلب از امکانات انتقال که توسط شرکتهای مخابراتی ارائه می شود، مانند شرکت های تلفن استفاده می کند. فن آوری های WAN به طور کلی در سه لایه پایین مدل مرجع OSI کار می کنند: لایه فیزیکی، لایه پیوند داده و لایه شبکه.
شبکه خصوصی سازمانی (Enterprise private)
یک شبکه خصوصی سازمانی شبکه ای است که یک سازمان واحد برای اتصال محل های دفاتر خود (به عنوان مثال، سایت های تولید، دفاتر مرکزی، دفاتر از راه دور، مغازه ها) ایجاد می کند تا آنها بتوانند منابع رایانه ای را به اشتراک بگذارند.
شبکه خصوصی مجازی (Virtual private Network)
یک شبکه خصوصی مجازی (VPN) یک شبکه پوشش است که در آن برخی از پیوندها بین گره ها به جای سیم های فیزیکی توسط اتصالات باز یا مدارهای مجازی در برخی از شبکه های بزرگتر (به عنوان مثال اینترنت) انجام می شود. گفته می شود پروتکل های لایه پیوند داده شبکه مجازی در این حالت از طریق شبکه بزرگتر تونل می شوند. یک برنامه مشترک ارتباطات ایمن از طریق اینترنت عمومی است، اما یک VPN نیازی به ویژگی های امنیتی صریح مانند تأیید اعتبار یا رمزگذاری محتوا ندارد. به عنوان مثال، VPN ها می توانند برای جدا کردن ترافیک جوامع مختلف کاربر از طریق شبکه زیربنایی با ویژگی های امنیتی قوی مورد استفاده قرار گیرند. VPN ممکن است عملکرد بهترین تلاش را داشته باشد یا ممکن است توافق سطح خدمات تعریف شده ای (SLA) بین کلاینت VPN و ارائه دهنده خدمات VPN داشته باشد. به طور کلی، یک VPN دارای توپولوژی پیچیده تر از نقطه به نقطه است.
شبکه منطقه جهانی (Global area)
شبکه منطقه جهانی (GAN) شبکه ای است که برای پشتیبانی از موبایل از طریق تعداد دلخواه شبکه های بی سیم، مناطق تحت پوشش ماهواره ای و غیره استفاده می شود. چالش اصلی ارتباطات موبایل انتقال ارتباطات کاربر از یک منطقه تحت پوشش محلی به دیگری است. در IEEE Project 802، این شامل جانشینی از شبکه های وایرلس زمینی است.
طراحی شبکه
شبکه های رایانه ای می توانند طراحی های متفاوتی داشته باشند که دو شکل اصلی آن عبارتند از کلاینت / سرور و شبکه های Peer-to-peer. شبکه های کلاینت / سرور دارای سرورهای متمرکز برای ذخیره سازی هستند که توسط رایانه ها و دستگاه های کلاینت قابل دسترسی هستند. شبکه های Peer-to-peer تمایل دارند دستگاه هایی داشته باشند که عملکردهای مشابه را پشتیبانی می کنند. آنها در خانه ها بیشتر دیده می شوند، در حالی که احتمالاً شبکه های کلاینت / سرور توسط مشاغل مورد استفاده قرار می گیرد.
دامنه سازمانی شبکه

شبکه ها معمولاً توسط سازمانهایی که صاحب آنها هستند اداره می شوند. شبکه های شرکت های خصوصی ممکن است از ترکیبی از اینترانت و اکسترانت استفاده کنند. آنها همچنین ممکن است دسترسی به شبکه به اینترنت داشته باشند، که هیچ مالک واحدی ندارد و تقریباً امکان اتصال جهانی نامحدود را فراهم می کند.
اینترانت
Intranet مجموعه ای از شبکه ها است که تحت کنترل یک نهاد اداری واحد قرار دارند. این اینترانت از پروتکل IP و ابزارهای مبتنی بر IP مانند مرورگرهای وب و برنامه های انتقال فایل استفاده می کند. نهاد اداری استفاده از اینترنت را در اختیار کاربران مجاز خود قرار می دهد. معمولاً یک اینترانت شبکه داخلی یک سازمان است. یک اینترانت بزرگ معمولاً حداقل دارای یک سرور وب است تا اطلاعات سازمانی را در اختیار کاربران قرار دهد. یک اینترانت همچنین پشت هر روتر در یک شبکه محلی قرار دارد.
اکسترانت
یک اکسترانت شبکه ای است که همچنین تحت کنترل اداری یک سازمان واحد است، اما از اتصال محدود به یک شبکه خارجی خاص پشتیبانی می کند. به عنوان مثال، یک سازمان ممکن است به برخی از جنبه های اینترانت خود دسترسی داشته باشد تا داده ها را با شرکای تجاری یا مشتریان خود به اشتراک بگذارد. این نهادهای دیگر لزوماً از منظر امنیتی مورد اعتماد نیستند. اتصال شبکه به یک اکسترانت اغلب، اما نه همیشه، از طریق فناوری WAN اجرا می شود.
شبکه تقابلی
شبکه تقابلی اتصال چندین شبکه رایانه ای از طریق یک فناوری مسیریابی مشترک با استفاده از روتر است.
اینترنت
نقشه جزئی اینترنت مبتنی بر داده های 15 ژانویه 2005 که در opte.org یافت شده است. هر خط بین دو گره ترسیم می شود و دو آدرس IP را نشان می دهد. طول خطوط نشانگر تأخیر بین آن دو گره است. این نمودار کمتر از 30٪ از شبکه های کلاس C قابل دستیابی را نشان می دهد. اینترنت بزرگترین نمونه کار اینترنتی است. این یک سیستم جهانی از شبکه های رایانه ای دولتی، دانشگاهی، شرکتی، عمومی و خصوصی بهم پیوسته است. این مبتنی بر فناوری های شبکه سازی مجموعه پروتکل اینترنت است. این جانشین شبکه آژانس پروژه های تحقیقاتی پیشرفته (ARPANET) است که توسط دارپا وزارت دفاع ایالات متحده ساخته شده است. اینترنت از ارتباطات مش و Backbone شبکه نوری برای فعال کردن شبکه جهانی وب (WWW)، اینترنت اشیاء، انتقال فیلم و طیف گسترده ای از خدمات اطلاعاتی استفاده می کند.
شرکت کنندگان در اینترنت از روش های متنوعی از چند صد پروتکل مستند و معمولاً استاندارد سازگار با پروتکل اینترنت سوئیت و یک سیستم آدرس دهی (آدرس های IP) استفاده شده توسط اداره اعداد اختصاصی اینترنت و ثبت های آدرس استفاده می کنند. ارائه دهندگان خدمات و شرکت های بزرگ اطلاعات را در مورد میزان دسترسی به آدرس های خود از طریق پروتکل Border Gateway رد و بدل می کنند و یک شبکه مشرف به کار در مسیرهای انتقال را تشکیل می دهند.
دارک نت (Darknet)
دارک نت (Darknet) شبکه ای است که معمولاً از طریق اینترنت در حال اجرا است و فقط از طریق نرم افزار تخصصی قابل دسترسی است. darknet یک شبکه ناشناس است که در آن اتصالات فقط بین peers قابل اعتماد، که گاهی به آنها "دوستان" (F2F) گفته می شود، با استفاده از پروتکل ها و پورت های غیر استاندارد است. Darknets با دیگر شبکه های همکار توزیع شده متمایز است زیرا اشتراک گذاری ناشناس است (یعنی آدرس های IP به صورت عمومی به اشتراک گذاشته نمی شوند)، و بنابراین کاربران می توانند با ترس کمی از دخالت های دولتی یا شرکت ها، ارتباط برقرار کنند.
گواهینامه ها و آزمون های شبکه
کامپتیا (CompTIA) یک انجمن تجارت غیرانتفاعی است که صدور گواهینامه های حرفه ای برای صنعت فناوری اطلاعات (IT) صادر می کند. این یکی از انجمن های برتر تجاری صنعت IT به حساب می آید. CompTIA مستقر در Downers Grove ،Illinois در بیش از 120 کشور دارای گواهینامه های حرفه ای بی طرف از فروشنده است. این سازمان سالانه بیش از 50 مطالعه صنعت منتشر می کند تا روند و تغییرات صنعت را ردیابی کند. CompTIA، انجمن برتر فناوری جهان، رهبر فکر و رفتار است. از انجمن حرفه ای جدید فناوری اطلاعات گرفته تا برنامه های صدور گواهینامه برتر و همچنین تحقیقات اصلی برای انجمن ها و مجامع عضو، برنامه های آن، استانداردهای صنعت را تنظیم می کنند و رشد مهارت ها را تقویت و هر روز دانش و بینش ایجاد می کنند.
برنامه صدور گواهینامه DevNet جدید برای Cisco، توسعه دهنده نرم افزار، مهندسین DevOps، متخصصان اتوماسیون و سایر مهارتهای حرفه ای نرم افزار را تأیید می کند. گواهینامه تخصصی دانش شما را در مورد توانایی های فنی کلیدی در حال ظهور برنامه های کاربردی، اتوماسیون و زیرساخت های شبکه، اینترنت اشیا (IoT)، دواپس (DevOps) و Cloud اثبات می کند. گواهینامه های DevNet دانش شما در مورد توسعه و طراحی نرم افزار را آزمایش می کنند.
گواهینامه های آزمون های شبکه عبارتند از:
- (Juniper Networks Certified Internet Associate or Specialist (JNCIA/JNCIS
- (Network+ (CompTIA
- +CompTIA's Security
- (WCNA (Wireshark
- (Cisco Certified Network Professional (CCNP
- (Cisco Certified Internetwork Expert (CCIE
- (Cisco Certified Entry Networking Technician (CCENT
- (Cisco Certified Network Associate Routing and Switching (CCNA R&S
- (Cisco Certified Design Associate (CCDA
- (Cisco Certified Network Associate Cloud (CCNA Cloud
- (Cisco Certified Network Associate Data Center (CCNA Data Center
- (VMware Certified Professional 6 – Network Virtualization (VCP6-NV
- AWS Certified Solutions Architect